Manage Your Risk - All in One Place
A strategic approach to risk management that aligns with industry best practices and regulatory standards.
Cyber Risk Program
Build and manage a complete cybersecurity program from the ground up.
Crown Jewel Analysis (CJA)
Gain vital insights for planning future cyber defenses using our CJA.
Instant Assessments
Instantly build and customize your security program with our easy-to-use platform.
Risk Assessment Frameworks
Efficiently assess, prioritize, and mitigate risks using CIS CSC, NIST CSF, ISO27K, SOC2 and more.
Incident Response Manager
Effectively plan, respond, and recover from security incidents.
Third-Party Risk Management
Maintain a fortified defense across your supply chain.
Cyber Risk Dashboards
Advanced analytics that inform and empower strategic decision-making.
Seamless Integration
Automatically updates task management across modules, reducing manual effort.
Build Your Cybersecurity Strategy
Enveedo is the nerve center of your company’s cybersecurity program. And it’s never been more important to have one.
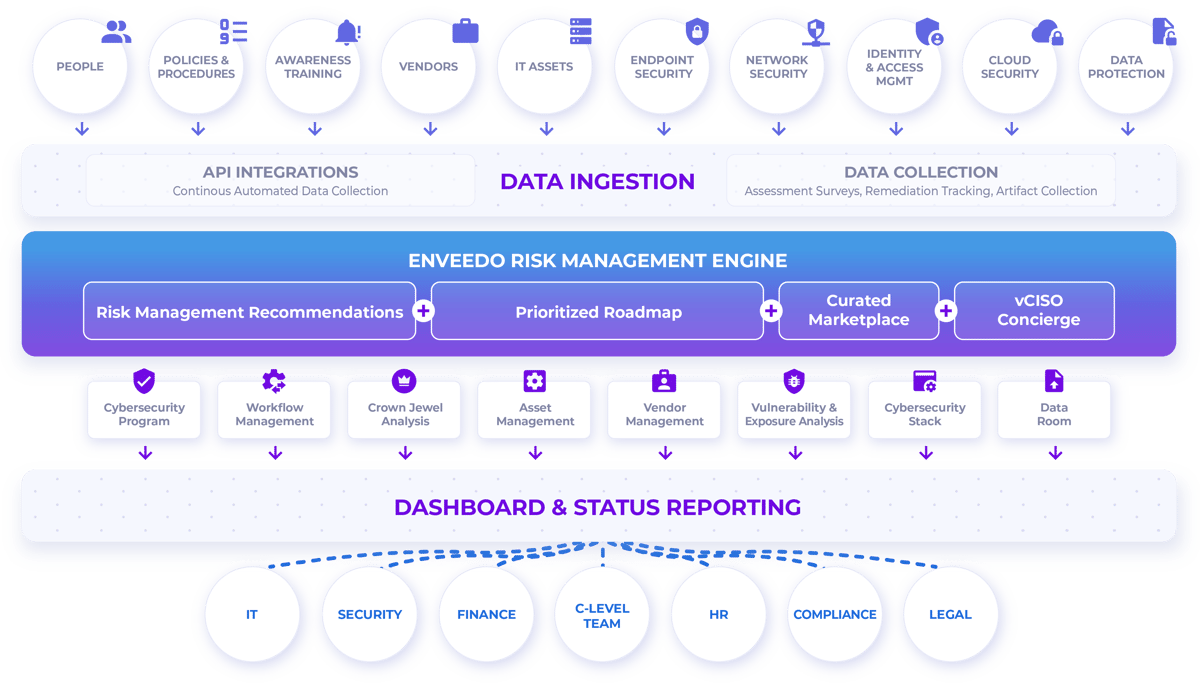
Ensure your organization's cybersecurity resilience
A strategic approach to risk management that aligns with industry best practices and regulatory standards. Trust Enveedo to illuminate the path to a secure, risk-aware future.

The Enveedo Advantage
Go beyond traditional platforms with a strategic partner that enhances your cybersecurity posture, ensuring you stay ahead of emerging threats.
CROWN JEWELS ANALYSIS
Understand What Matters the Most
With Enveedo's Crown Jewel Analysis, MSSPs can pinpoint and protect their clients' most vital information and business functions. Streamline integration of critical assets across security operations, enhancing risk management and compliance.


RISK ASSESSMENT
Identify & Assess Your Risk Posture
Navigate the complexities of cyber threats with Enveedo’s proactive Risk Assessment feature. Our advanced tools empower IT professionals to identify and evaluate potential risks, prioritizing them based on their impact on your business. Enveedo ensures you stay ahead of vulnerabilities, turning potential weaknesses into opportunities for strengthening your defenses.
WORKFLOW MANAGEMENT
Strategize & Prioritize Your Roadmap
Develop a comprehensive cybersecurity program with Enveedo’s comprehensive platform. From risk assessment and asset management to compliance tracking and incident response planning, Enveedo enables you to develop and manage an all-encompassing cybersecurity program seamlessly. Our integrated, automated approach provides a significant advantage over segmented and offline solutions offered by competitors, ensuring a more robust and responsive cybersecurity framework.


INCIDENT RESPONSE PLANNING READINESS
Be Prepared for the Worst
Comprehensive Planning and Support: Our Incident Response (IR) Manager module not only helps you craft a tailored Incident Response Plan but also integrates this planning with real-time data, ensuring you’re always prepared. With features like pre-defined communication templates and detailed incident tracking, Enveedo not only aids in efficient response but also ensures compliance with regulatory requirements.
CYBERSECURITY PERFORMANCE INDICATORS
Report with Clarity the Most
Enveedo’s centralized platform serves as a single source of truth for your risk posture, significantly reducing administrative, manual tasks and enhances the effectiveness of your security operations and communication where it matters most.

Channel Partners









Technology Partners





.png?width=1295&height=906&name=Strategy@2x-min-1%20(1).png)






